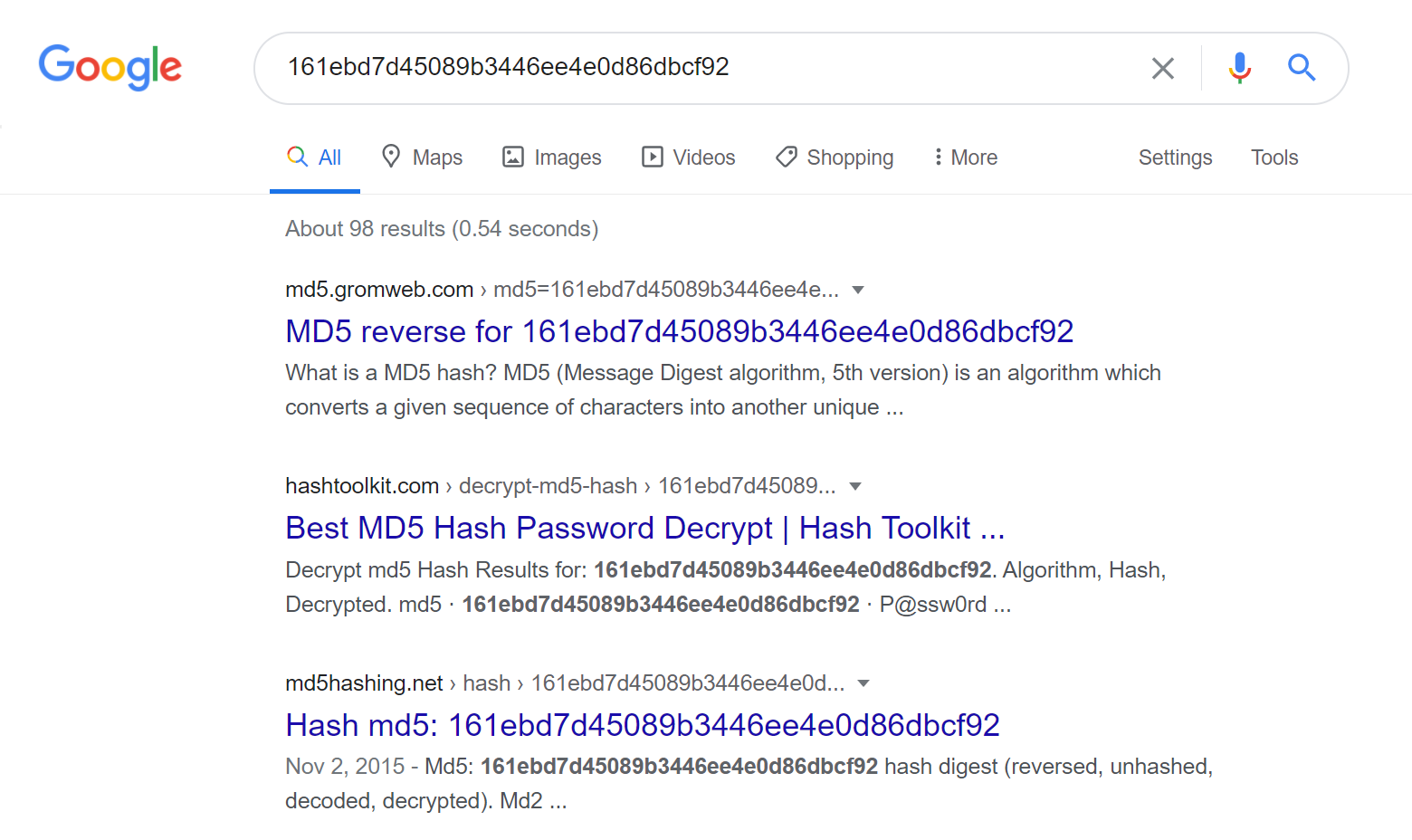
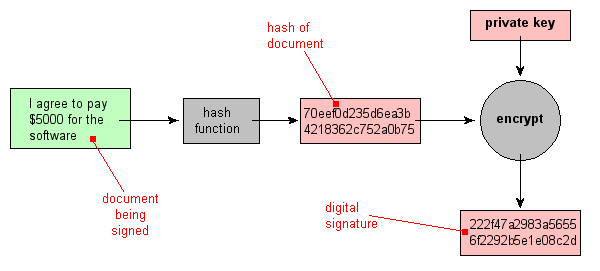
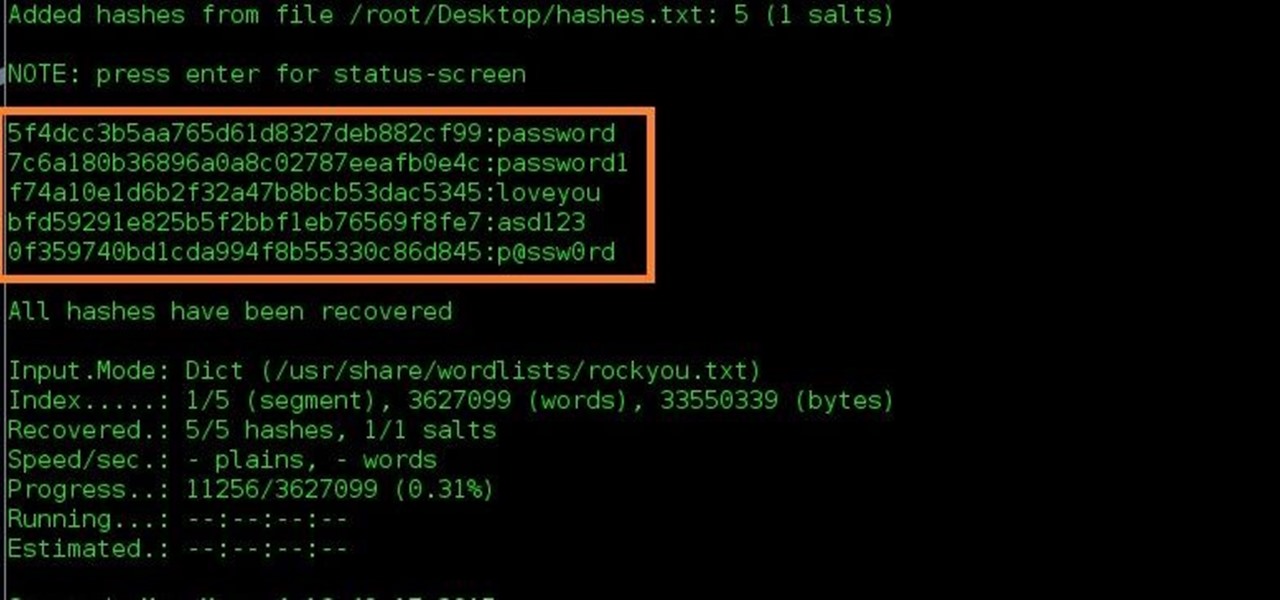
Password Hashes — How They Work, How They're Hacked, and How to Maximize Security | by Cassandra Corrales | Medium

Password Hashes — How They Work, How They're Hacked, and How to Maximize Security | by Cassandra Corrales | Medium

Cauliflower Hash Browns | Recipe | Cauliflower, Easy cauliflower recipes, Cauliflower hash brown recipe





![What Is Cryptographic Hash? [a Beginner's Guide] What Is Cryptographic Hash? [a Beginner's Guide]](https://techjury.net/wp-content/uploads/2020/06/hash-functions-speed-1024x753.png)